
Trusted Execution Technology:
One thing that is new with the 1333MHz FSB Core 2 Duo processors is Intel’s Trusted Execution Technology (TXT). This was formerly codenamed LaGrande Technology and is part of Intel’s Trusted Computing Initiative, which the company says is mainly focused around business users and the vPro platform.With this in mind, Intel has opted not to include TXT in its flagship Core 2 Extreme QX6850 as the Extreme series are designed for gamers and enthusiasts, while the mid-range processors are designed for all end users.
This is surprising and seems to highlight the fact that this is an optional feature that’s more business orientated than enthusiast orientated. Kentsfield is a pair of Conroe chips and in this particular case it’s a pair of 1333MHz FSB Core 2 Duos on the same chip packaging so it’s feasible that Intel could include the technology in a future stepping should it see the need to.
Intel describes the technology as “a concept of hardening the platform from software based attacks based on the expected behaviour of the platform and transactions.” Essentially, the computer will consistently behave in certain ways that are enforced by both hardware and software.
TXT is essentially a set of hardware extensions that work in conjunction with a Trusted Platform Module (TPM) chip and goes beyond the Non-execution bit that has been a feature on recent processors from both AMD and Intel. The TPM is disabled in the BIOS by default, as determined by the open specifications that are freely downloadable.
However, when it’s enabled, it allows your machine to generate secure keys while also having access to non-volatile memory that cannot be accessed by anyone that isn’t authenticated to access it. Normally you’d think “that’s hackable” right? Well, not only does the TMP use a 2048-bit encryption, the key is also not available to the owner of the machine as it never leaves the chip.
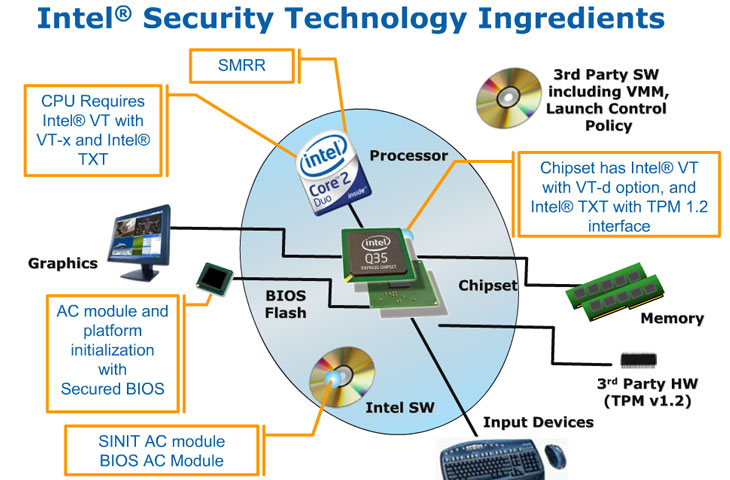
Intel Trusted Execution Technology requirements
Here’s a list of what TXT incorporates:
- Protected Execution: With this particular feature, TXT allows you to execute a supported application in an isolated environment, thus “protecting” it from other software running on the same machine while preventing potentially malicious software from monitoring and compromising the application or data produced by it. Even if multiple applications are running in Protected Execution mode, they’re unable to talk to one another as each application is allocated its own dedicated resources.
- Sealed Storage: This is a partition of non-volatile memory where Trusted Platform Module chips can store and encrypt keys, data and other sensitive information. The memory is not accessible from “the outside” and any attempts to copy data from the Trusted Platform Module will be scrambled. Thus, even if someone did manage to get hold of your data, they’d have to decrypt it – a task that can only be done in the same executing environment as the one where the data was encrypted (i.e. on the same machine with the same encryption key).
- Protected Input: Using Protected Input, TXT will prevent unauthorised monitoring of input devices like your keyboard and mouse. The input managers for both keyboard and mouse will be executed in isolation and inputs will be encrypted and are only accessible in applications that have the correct encryption key.
- Protected Graphics: For applications running in a Protected Execution environment, any data in the graphics card’s frame buffer must be encrypted and protected from unauthorised access. In addition, data moving to and from the frame buffer must also be encrypted.
- Attestation: This feature essentially monitors and assures the system that the Protected Execution environment has been correctly invoked and also provides a measurement of the software running in the Protected Execution environment.
- Protected Launch: This particular part of TXT will protect critical parts of the operating system and system software components during launch and registration in a Protected Execution environment.
The initiative has had its fair share of criticism though and most of that is because of Microsoft’s vision for the technology, which was to essentially lock down the system in such a manner that nothing would be able to escape the Trusted Platform Module (or Secure Crypto Processor, as Microsoft coined it). Trusted Execution Technology and thus the Trusted Platform Module are both related to Microsoft’s Palladium technology, because they would be something that Microsoft’s controversial vision could use do add another layer of DRM.
It’s fair to say that Microsoft’s actions have caused a lot of the controversy surrounding the whole Trusted Computing Initiative that engulfs Trusted Execution Technology because it has ultimately been tarred with the same brush. The things in the Trusted Computing Initiative that have caused a stir are all things that were discussed by Microsoft when it was talking about Palladium.
Things like revoking documents or emails aren’t a part of the TXT specifications, but it’s nevertheless worrying to think that TXT could be used to implement a more advanced and potentially tamper-resistant form of DRM.
For the most part though, what TXT actually offers could well be beneficial to businesses. However, as that’s not really our remit, the question is whether those potential benefits are advantageous in the enthusiast’s space. Hopefully, given the fact that the Core 2 Extreme QX6850 doesn’t have Trusted Execution Technology enabled, TXT isn’t a technology that is going to be “abused”. Indeed, during my discussions with Intel on the technology, the company was pretty adamant that TXT is a business-focused feature.

MSI MPG Velox 100R Chassis Review
October 14 2021 | 15:04








Want to comment? Please log in.